TL;DR
- Stealth Phishing Attacks – highly sophisticated attacks where attackers block any cloud-based service from seeing their phishing
page, and show it only to targeted victims on their devices in real-time when they click on the phishing link - Stealth phishing attacks have been on the rise for the past few years and have left most cloud-based anti-phishing services flying blind
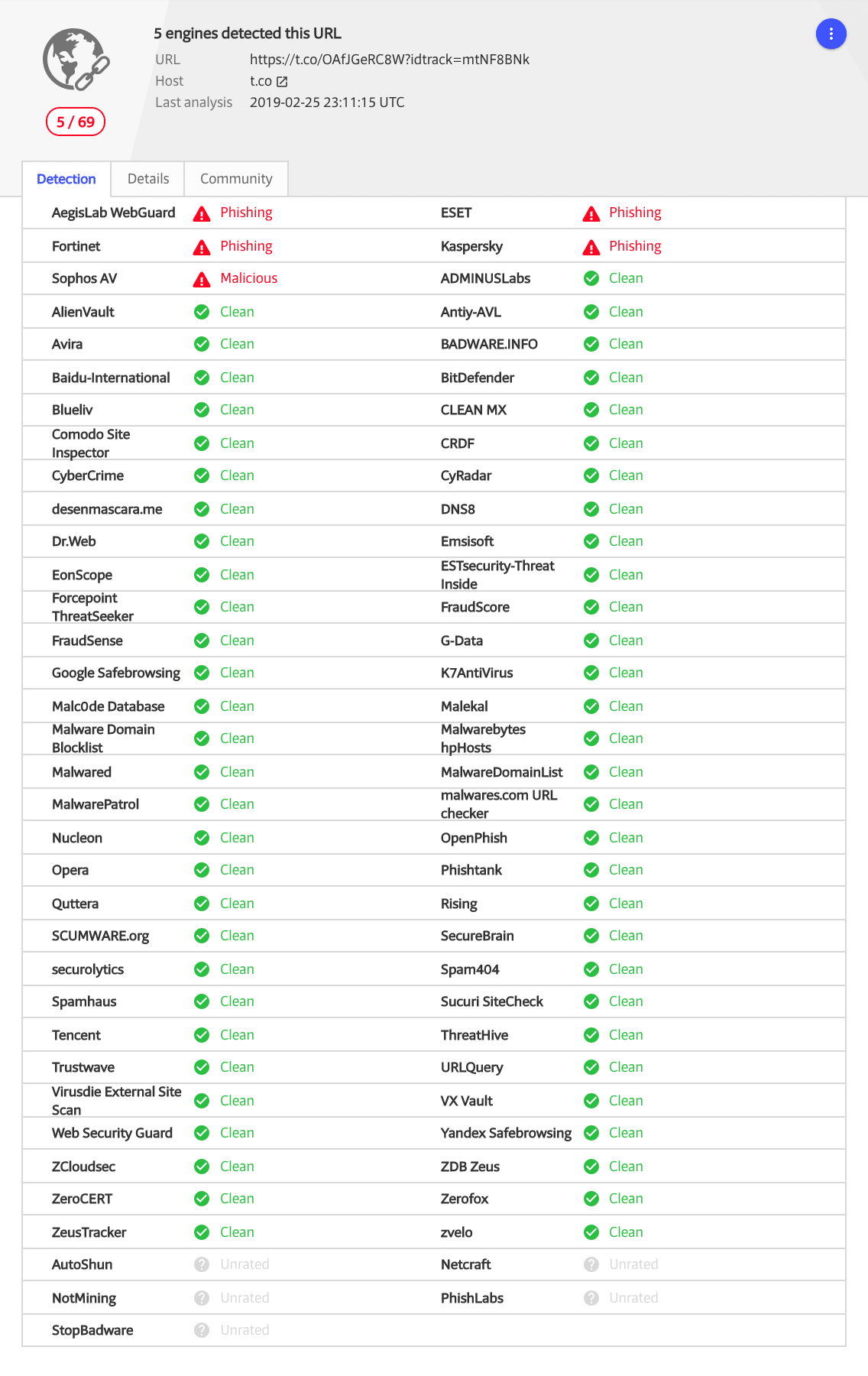
- This post shows one such actual stealth phishing attack with screenshots from various anti-phishing services calling it “safe” and not being able to see the attack page from the cloud
UPDATE 25 Feb 2019 – This attack is still not blacklisted, 9 days later, by most well-known cloud-based cybersecurity services as can be seen from the Virus Total scan done today.
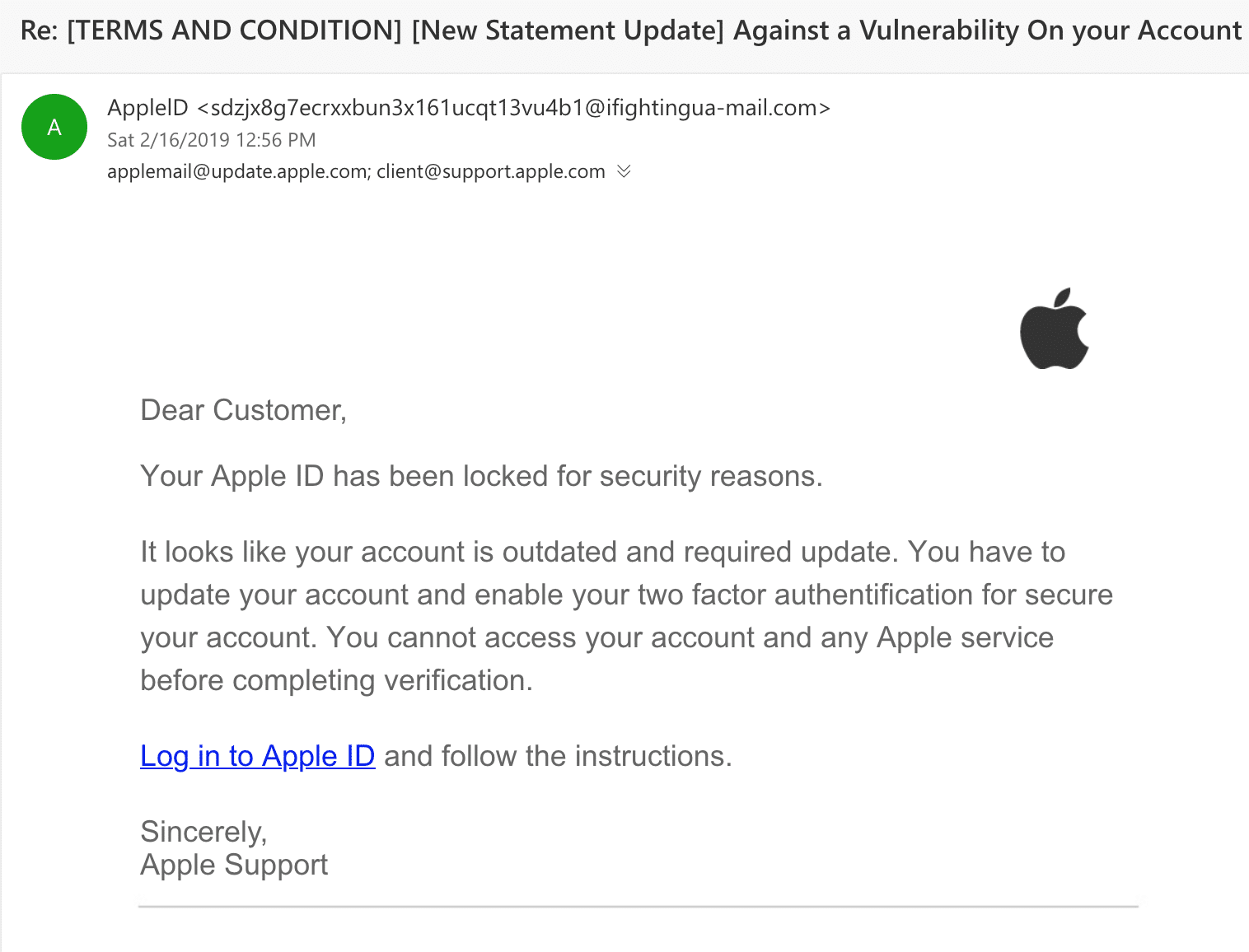
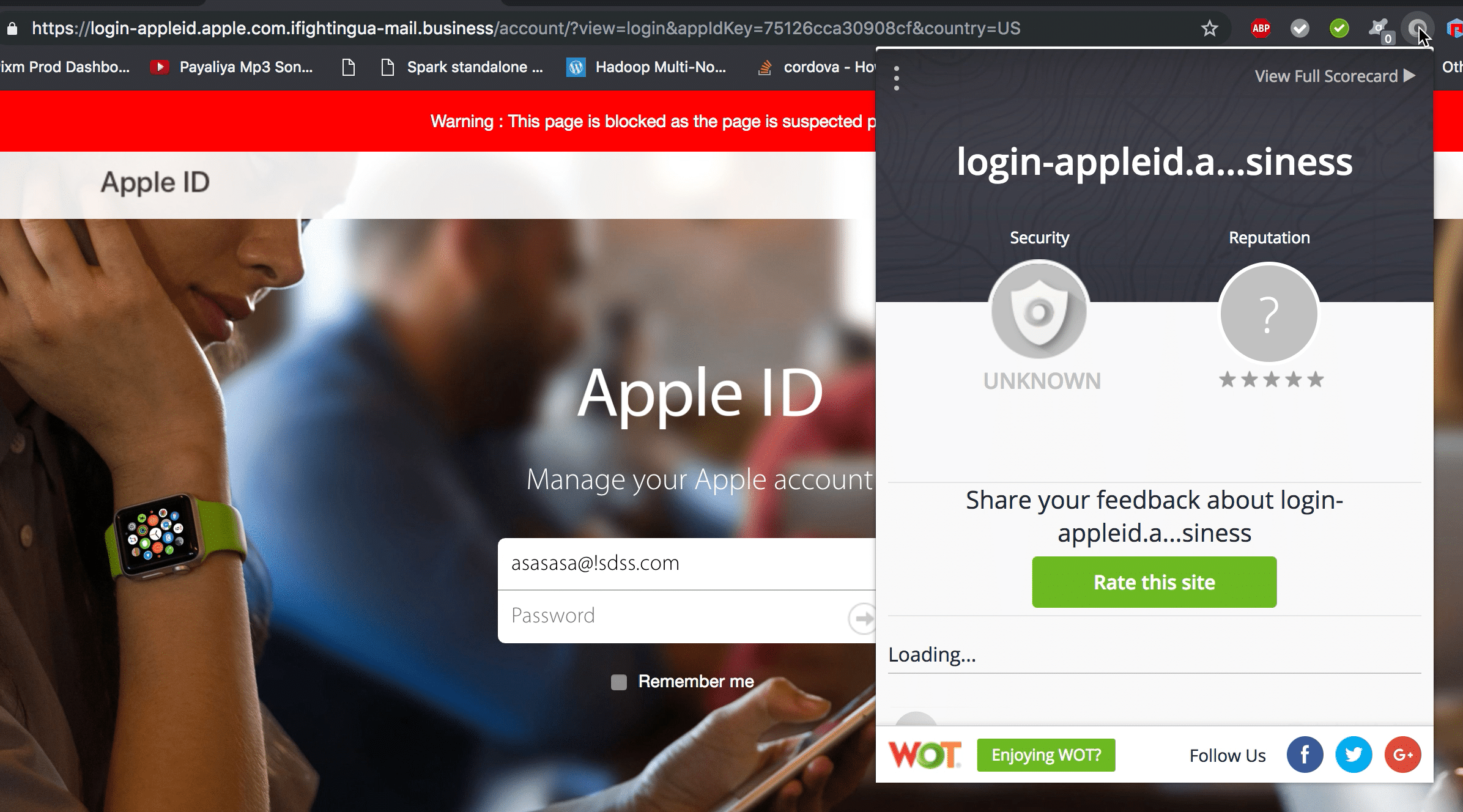
Today, I received an Apple phishing attack in my personal email account. While it looked like any regular phishing attempt, it was hardly that.
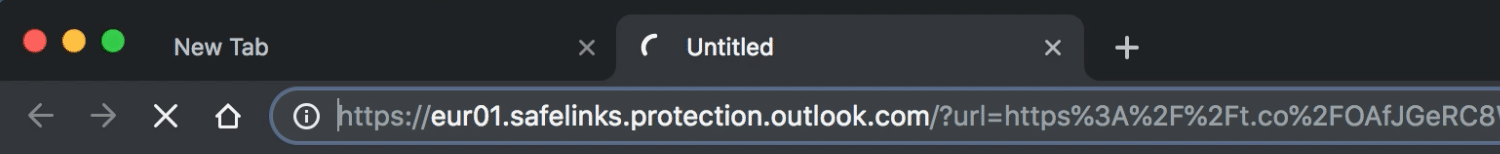
Office 365’s Real-time Safelinks Protection
With Pixm Anti-Phishing installed on my mac, I clicked on the link. Since my personal email is on Outlook.com, Office 365 provides built-in real-time link protection at the point of click. As you can see in the screenshot below, this phishing link initially gets scanned by Office 365’s Safelinks Protection but doesn’t get flagged and instead let’s it proceed to the link.
Pixm Shuts Down Phishing Attack at Point of Click
After the page finished loading and as soon as the page requests for sensitive information such as a password, Pixm jumped into action using deep learning computer vision, detected it as a phishing attack and shut it down immediately. Being on the endpoint gives Pixm the unique ability to analyze stealth webpages in real-time at the point of click. It also gives Pixm the ability to protect the user not just in their work email but also across personal email and common social/messaging platforms.
How Pixm Anti-Phishing works
Pixm uses deep learning computer vision in real-time to analyze the webpage visually (by taking a screenshot after the page finishes loading) to find out if it looks like the login page of a well-known brand (or a brand that Pixm recognizes). If so, it compares the domain of the website the user is currently on to the list of domains authorized by that brand to show a login page. If the current domain isn’t in that list, the page is shut down immediately where the user can no longer click or type on the page.
Stealth Phishing Attack – Invisible to Cloud-based Anti-Phishing
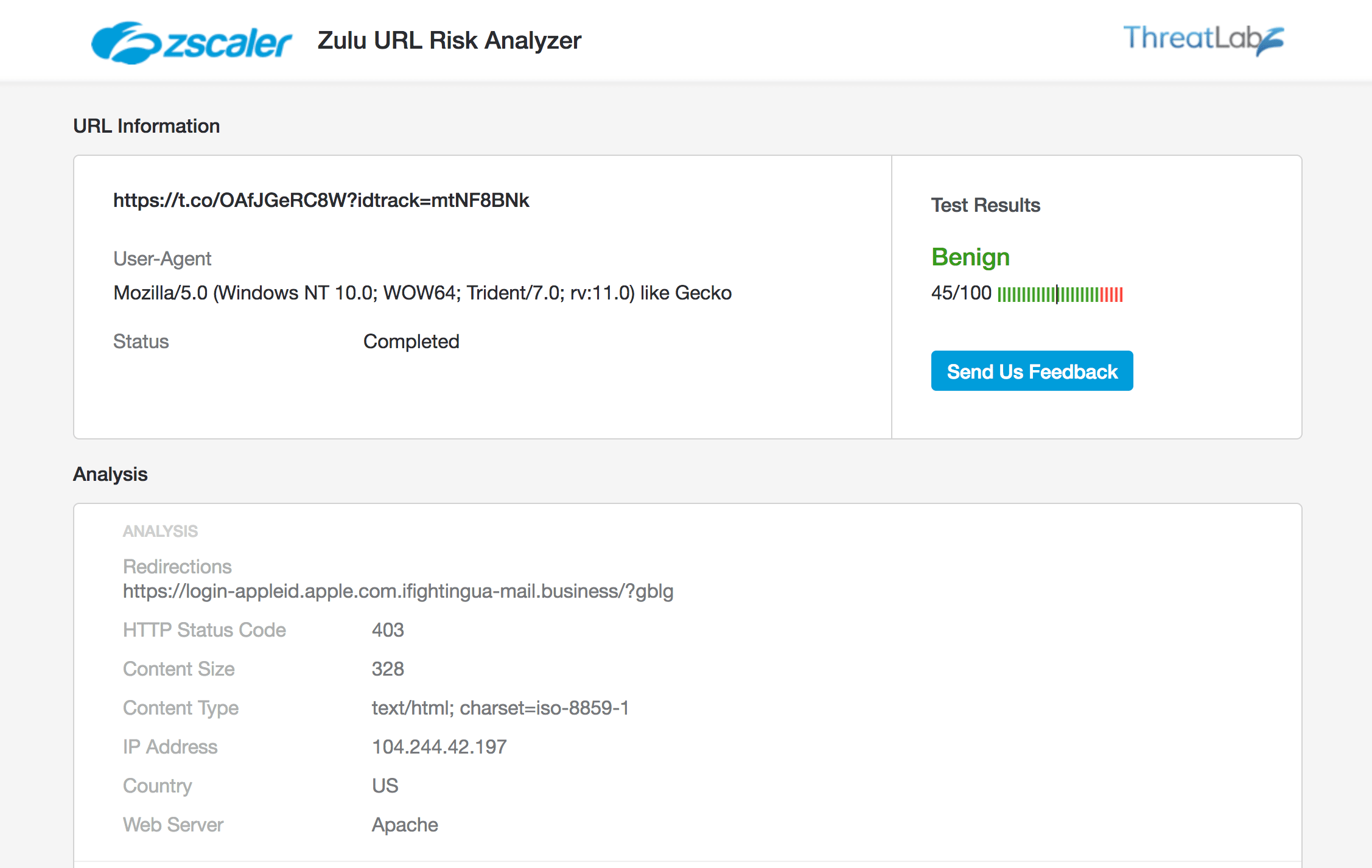
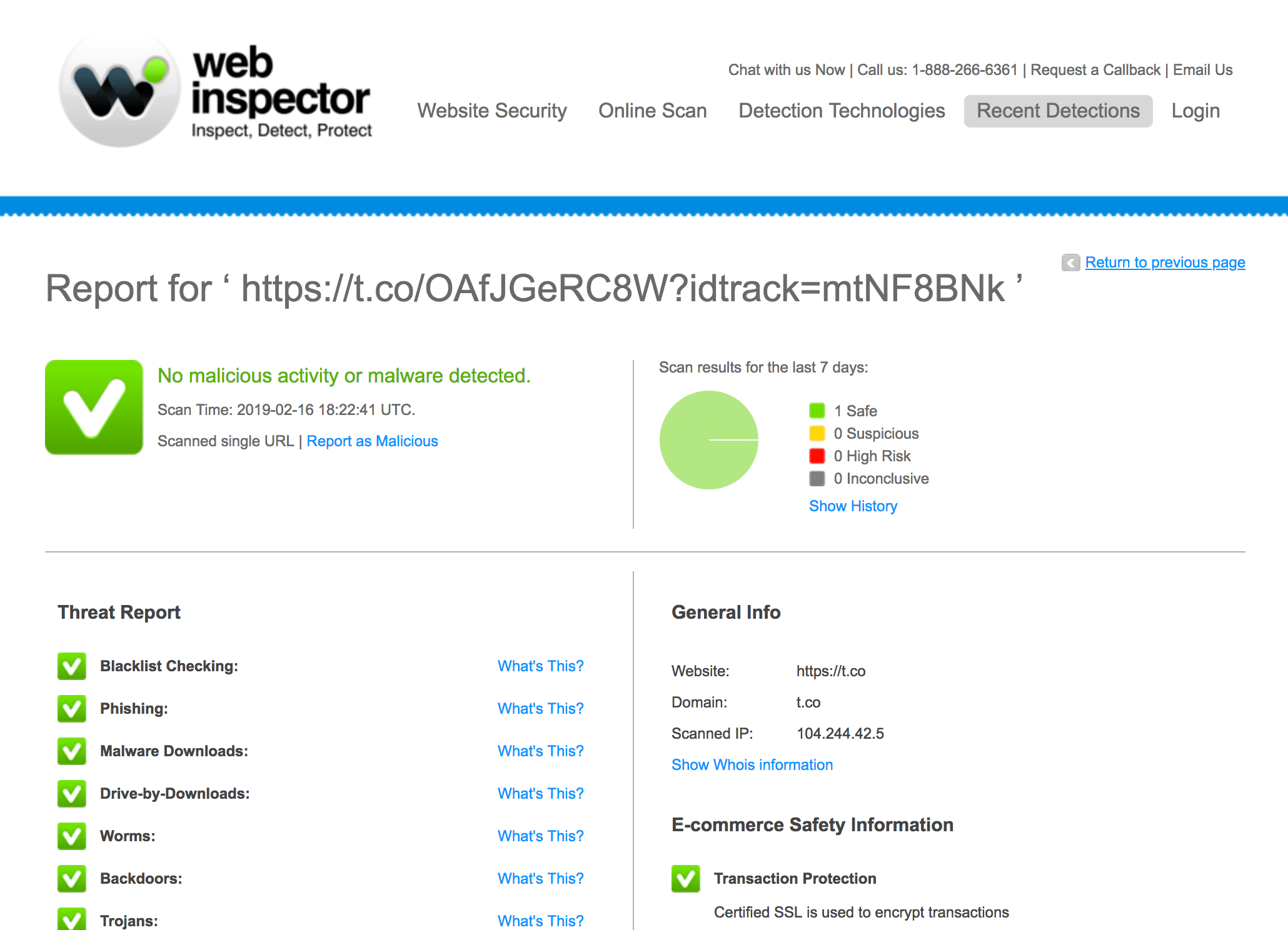
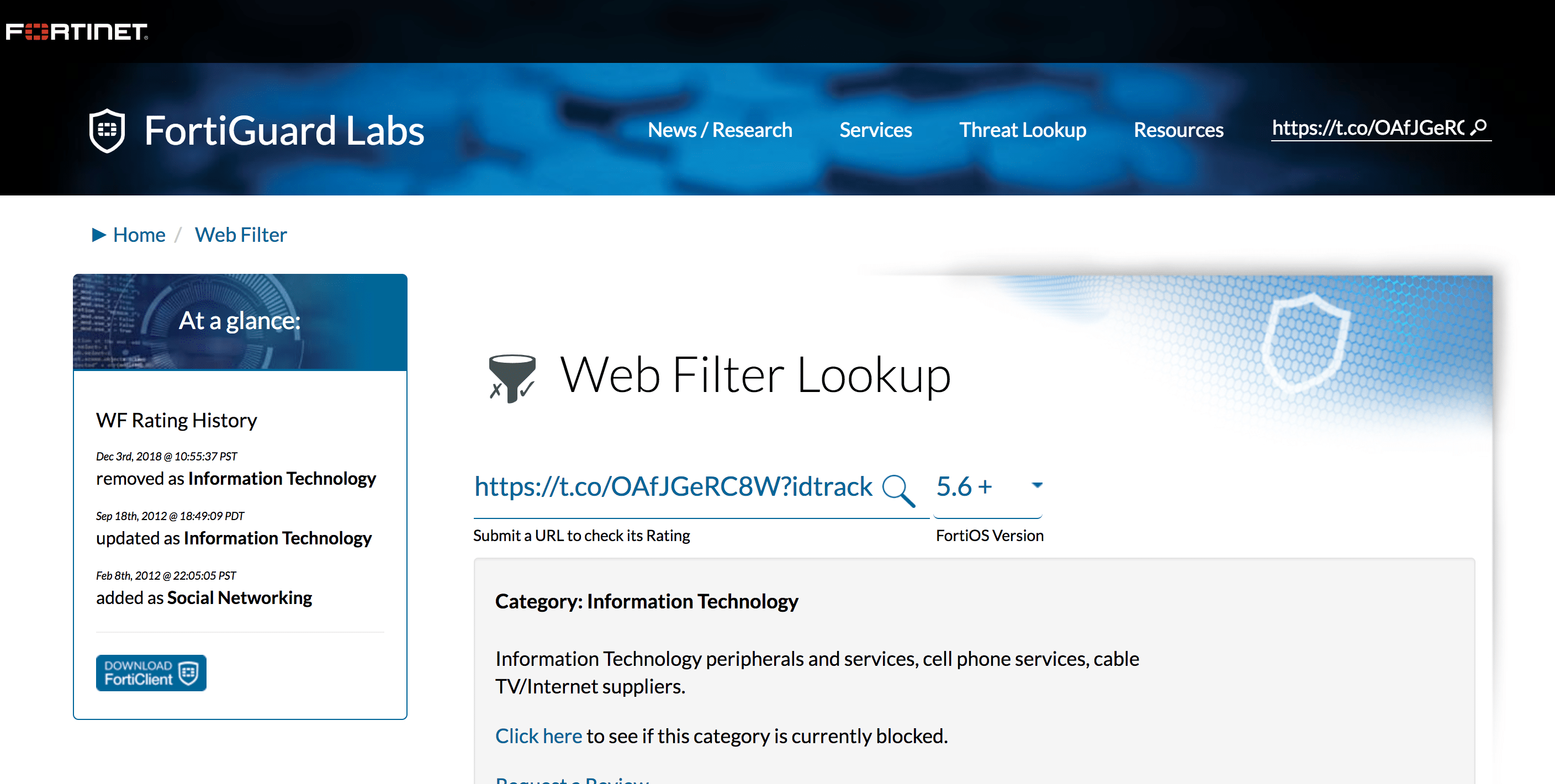
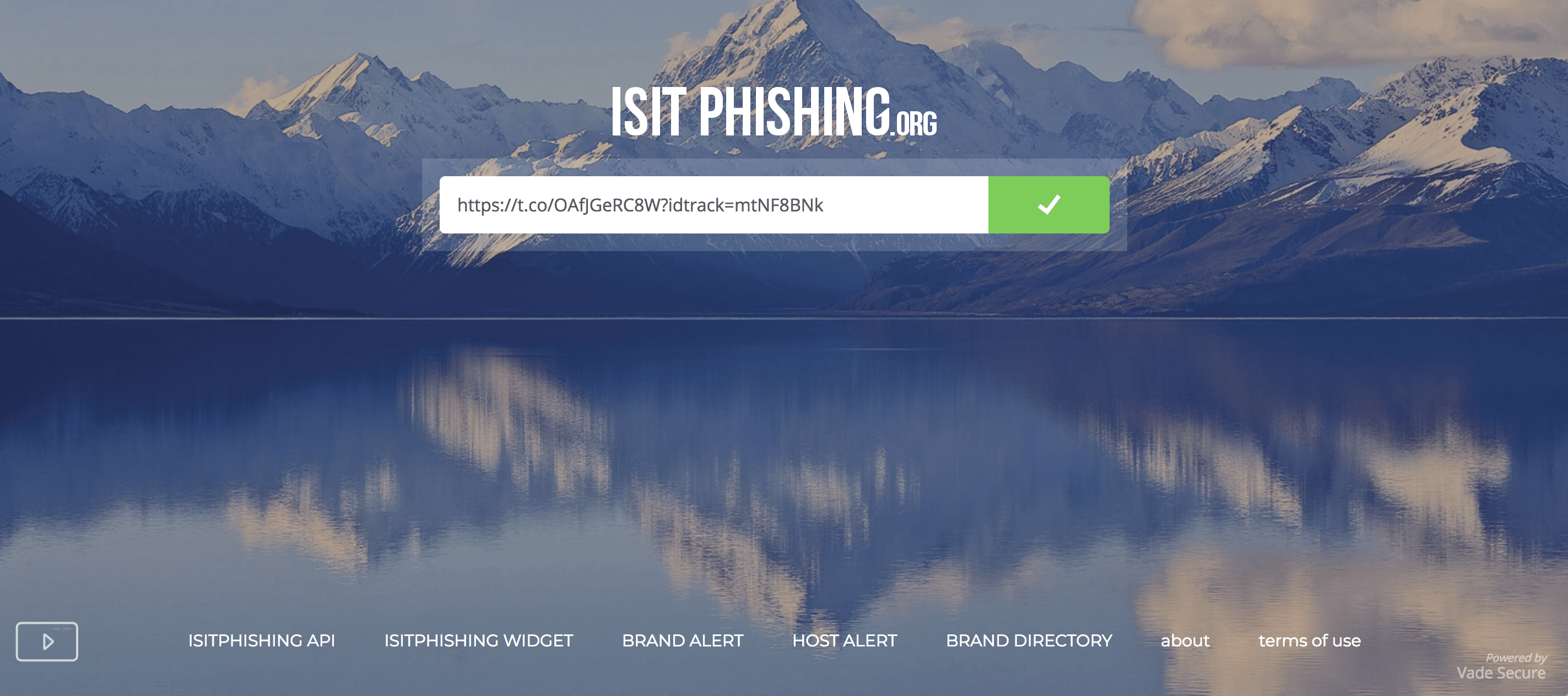
Cloud-based services have been blocked from being able to see this attack. This stealth functionality has already been or in the process of being incorporated into all phishing kits to render cloud-based anti-phishing services blind.
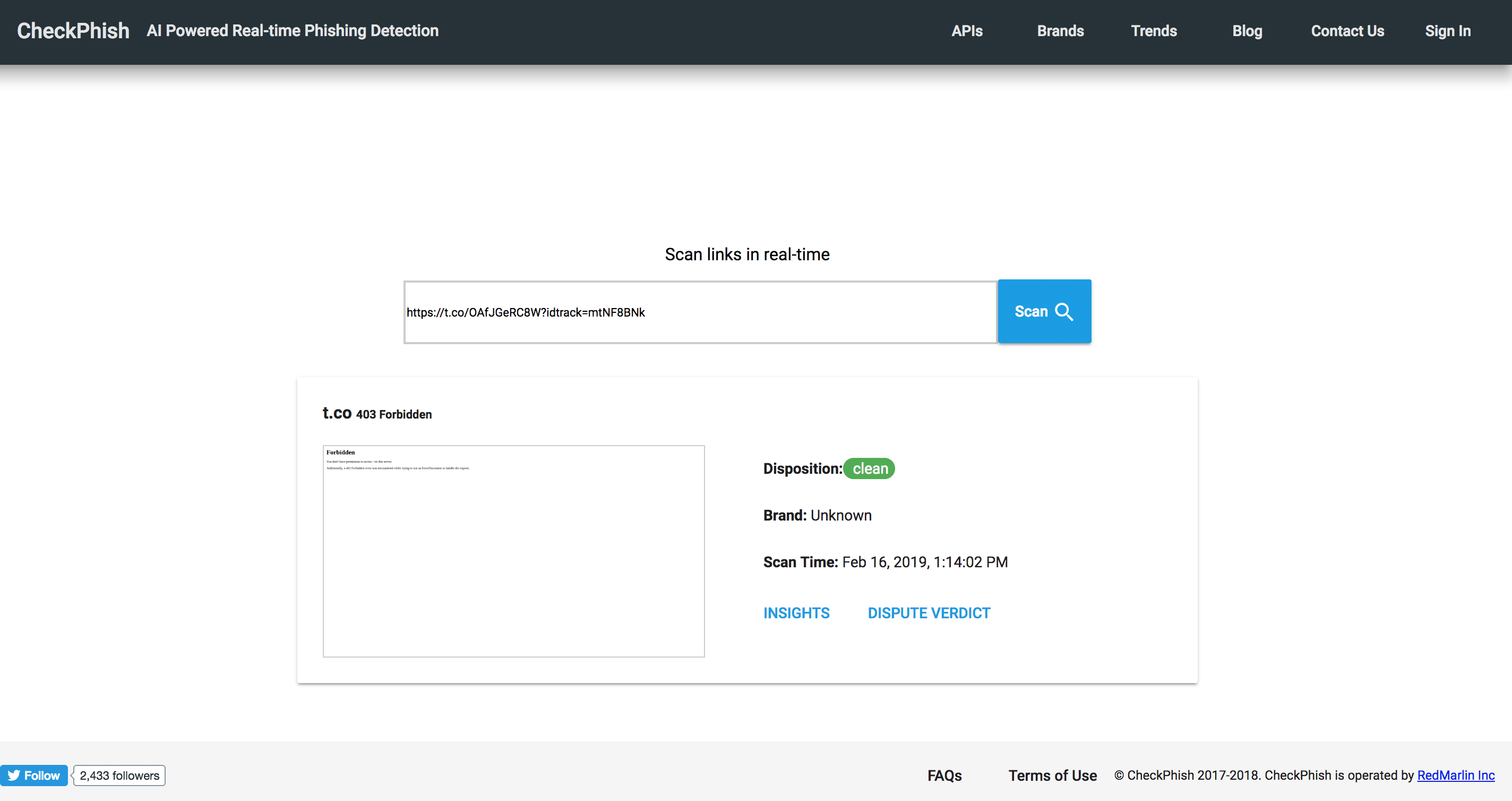
RedMarlin’s CheckPhish seeing “Forbidden”
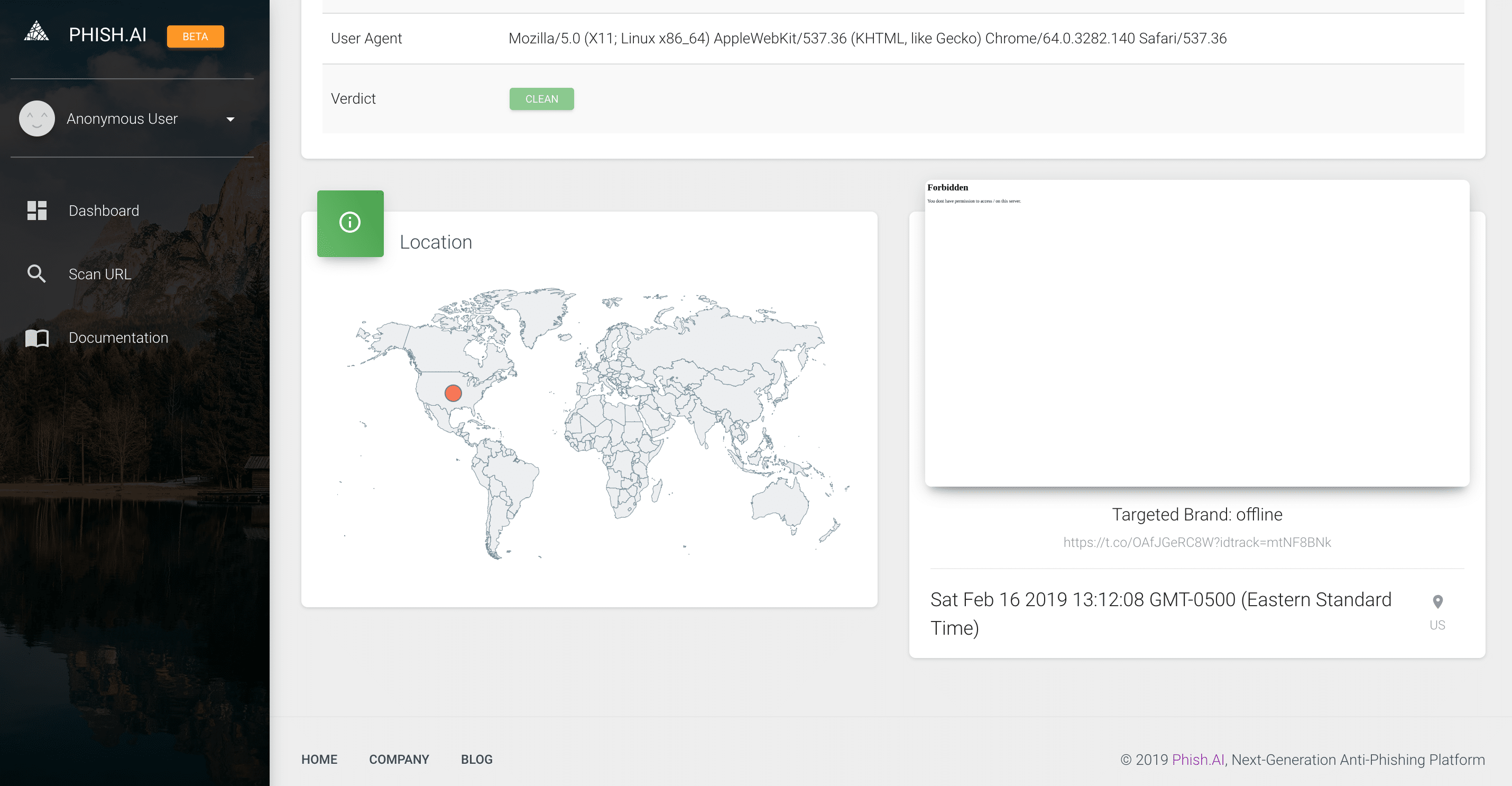
Phish.AI seeing “Forbidden”
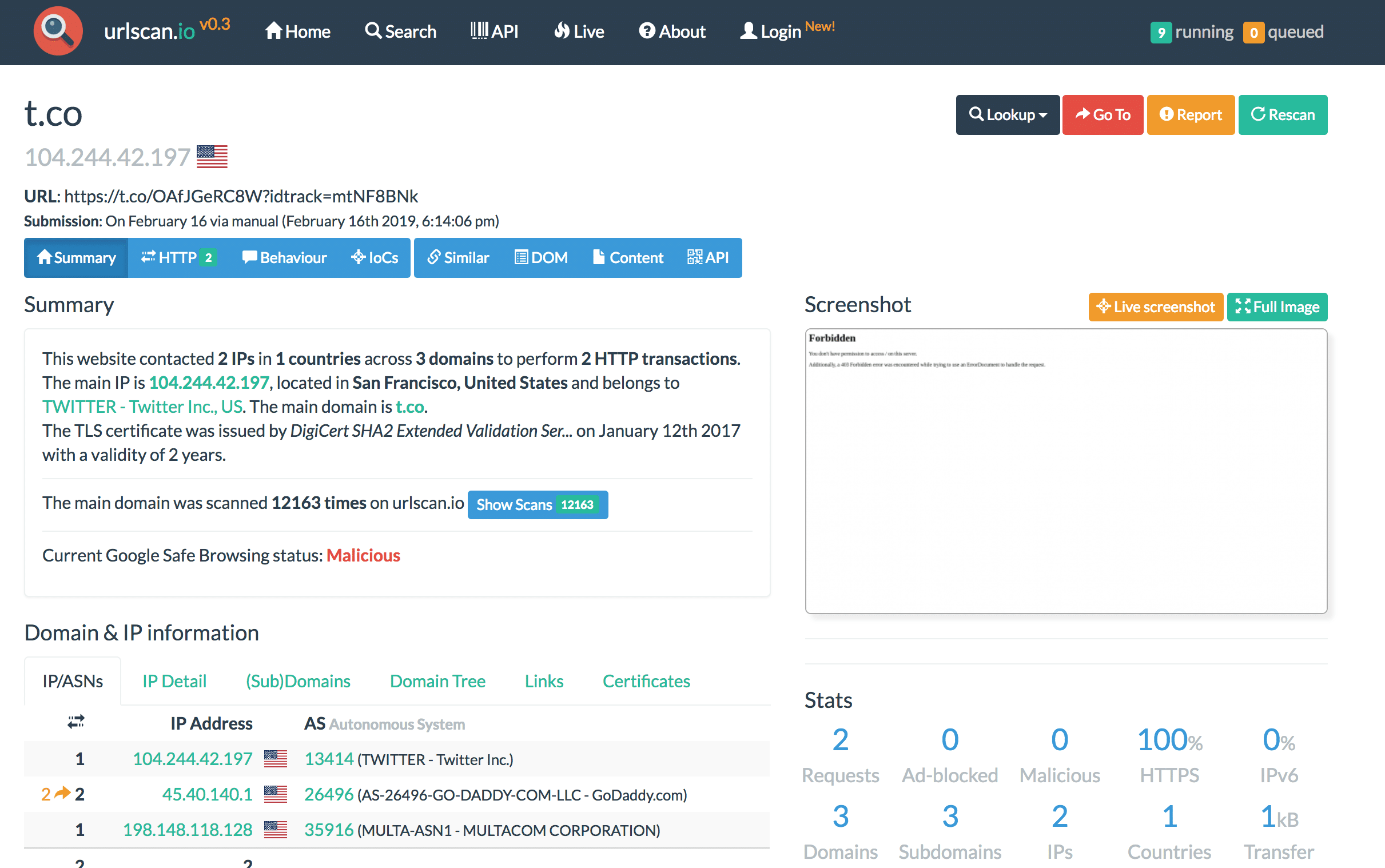
URLScan.io seeing “Forbidden”
WebOfTrust (WOT)
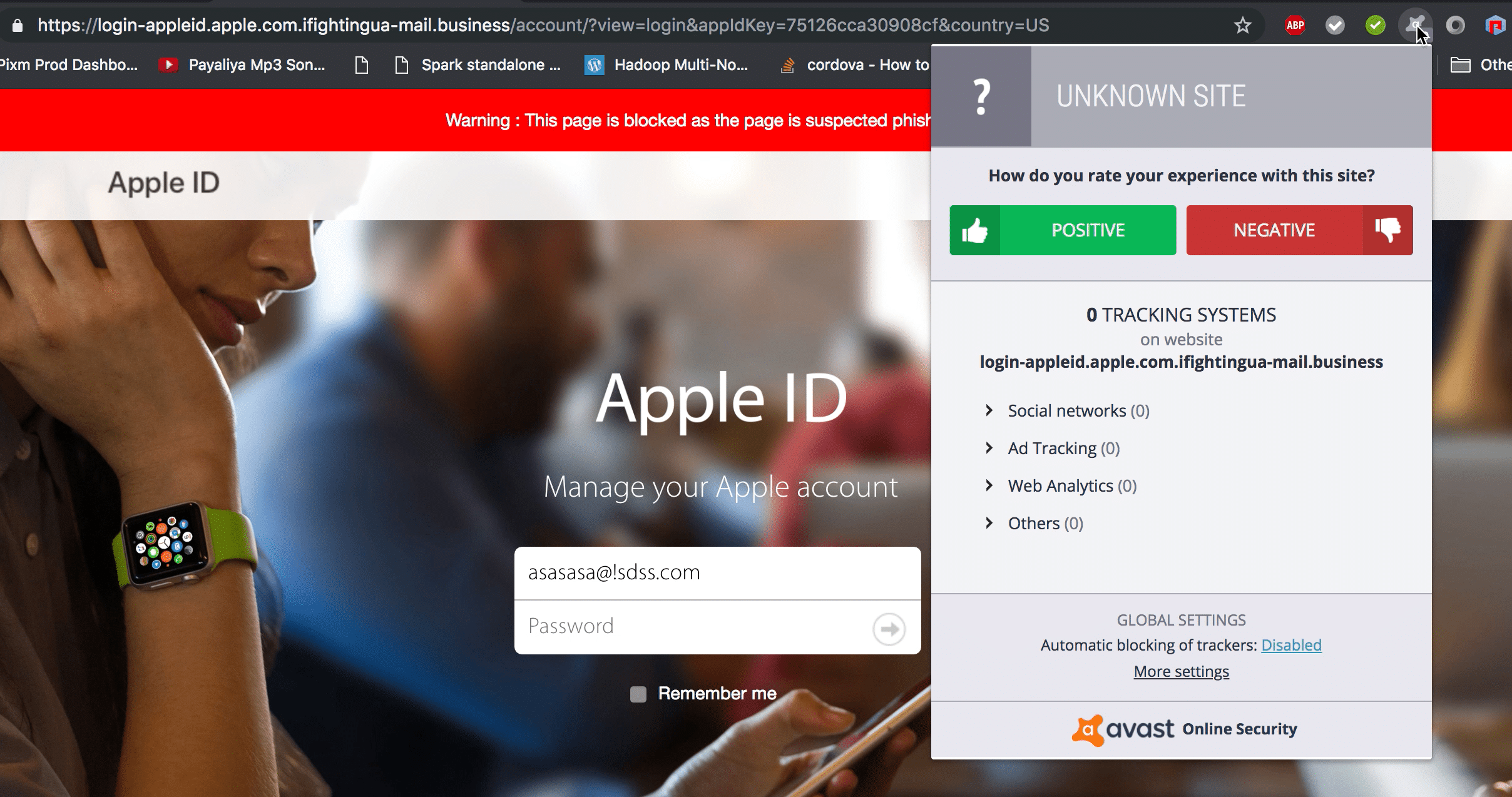
Avast Online Security
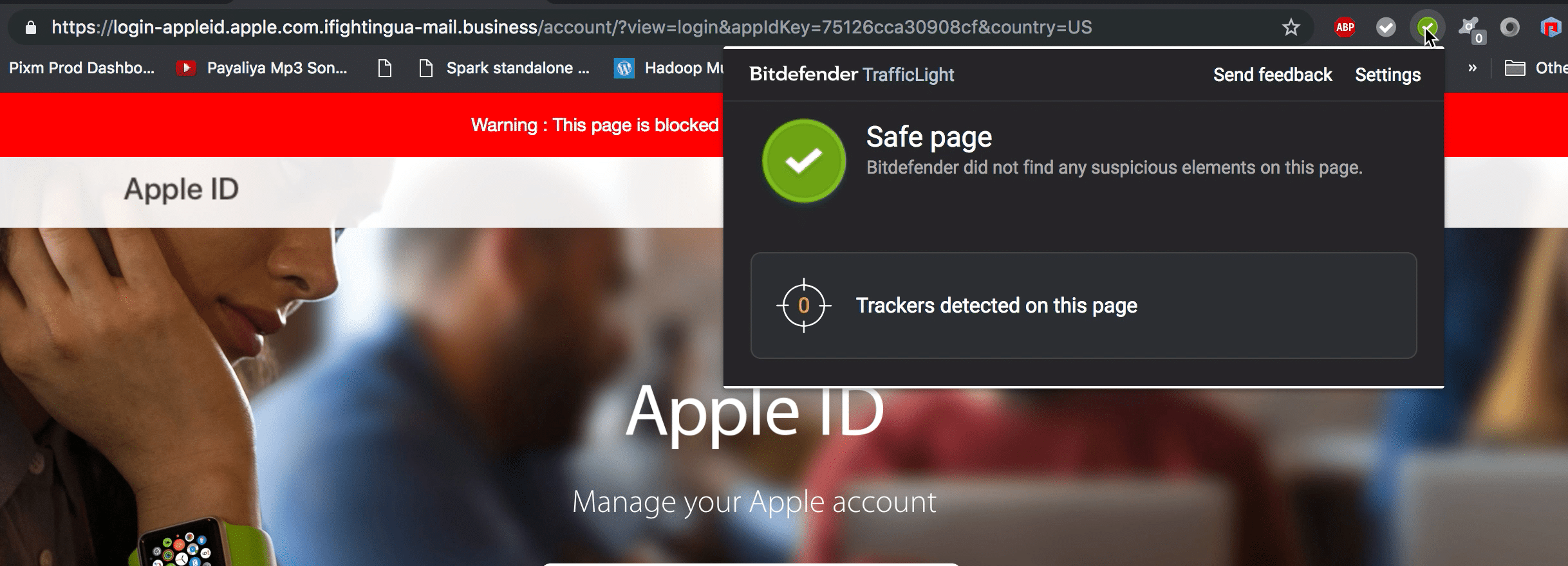
BitDefender TrafficLight
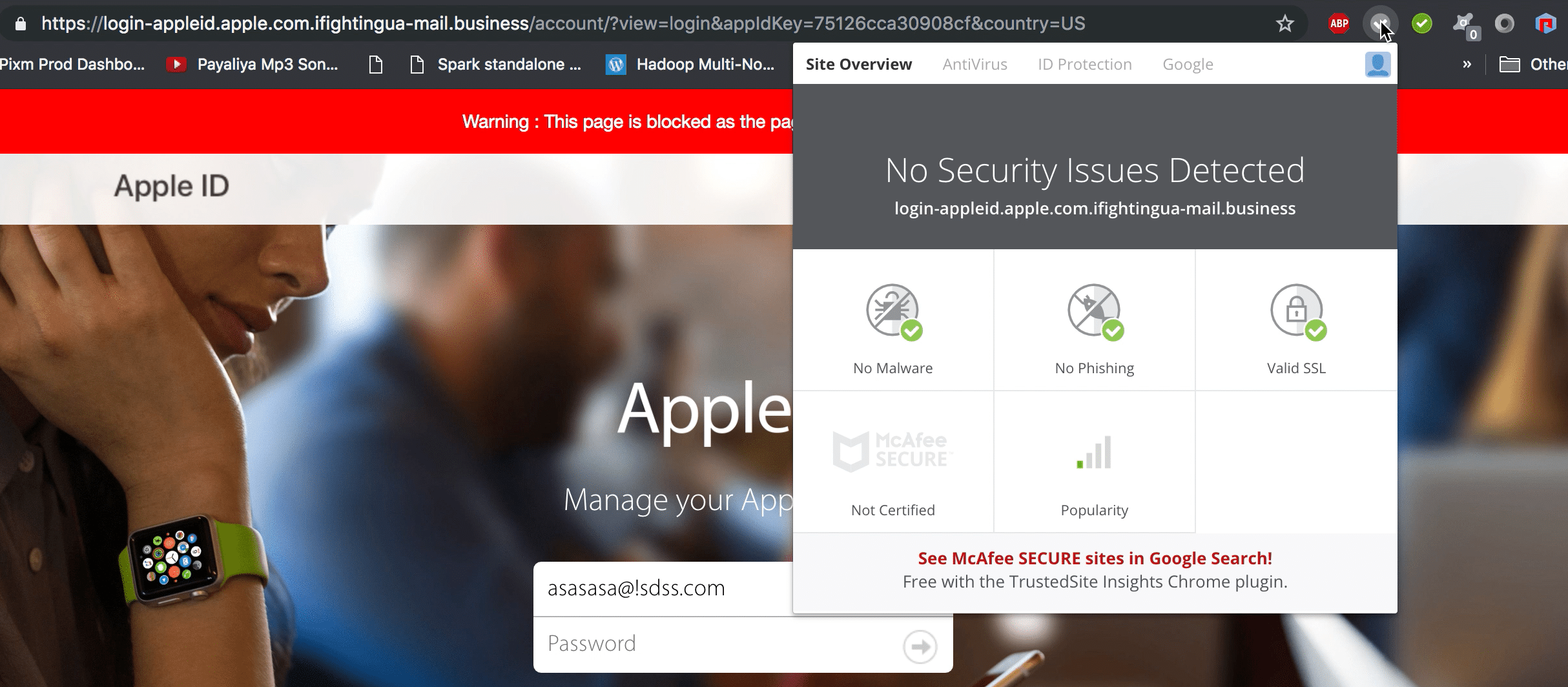
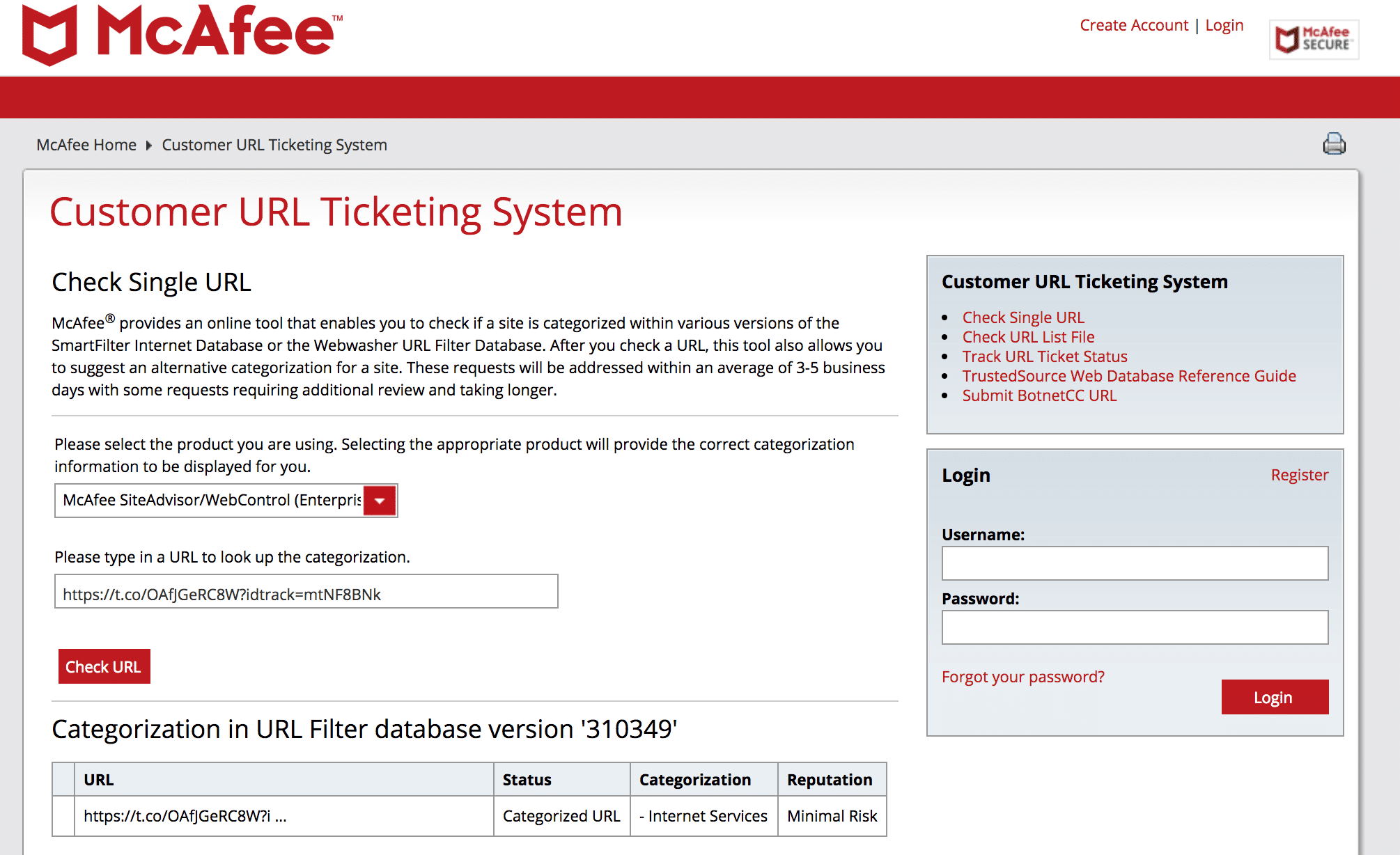
McAfee SECURE
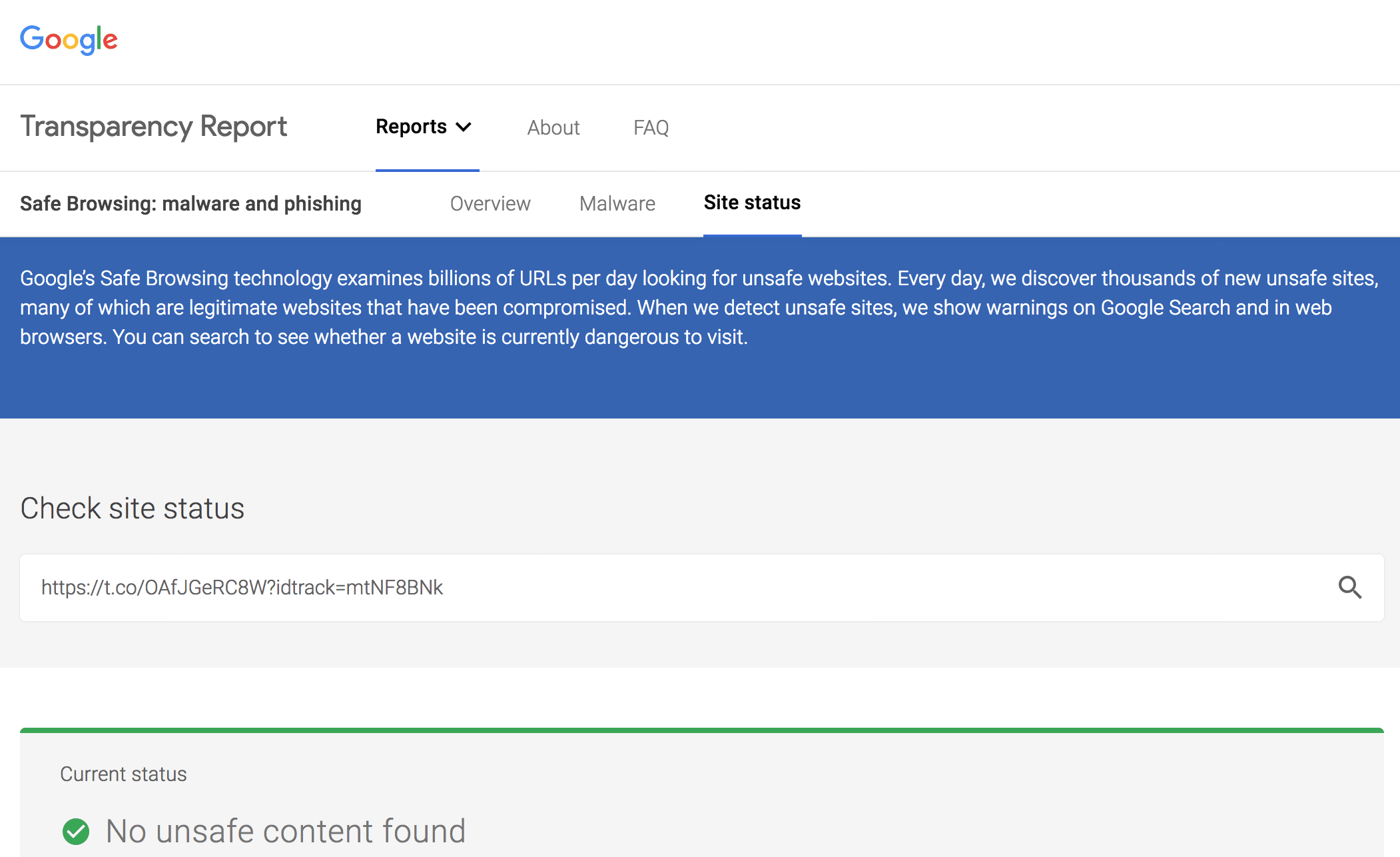
Google SafeBrowsing
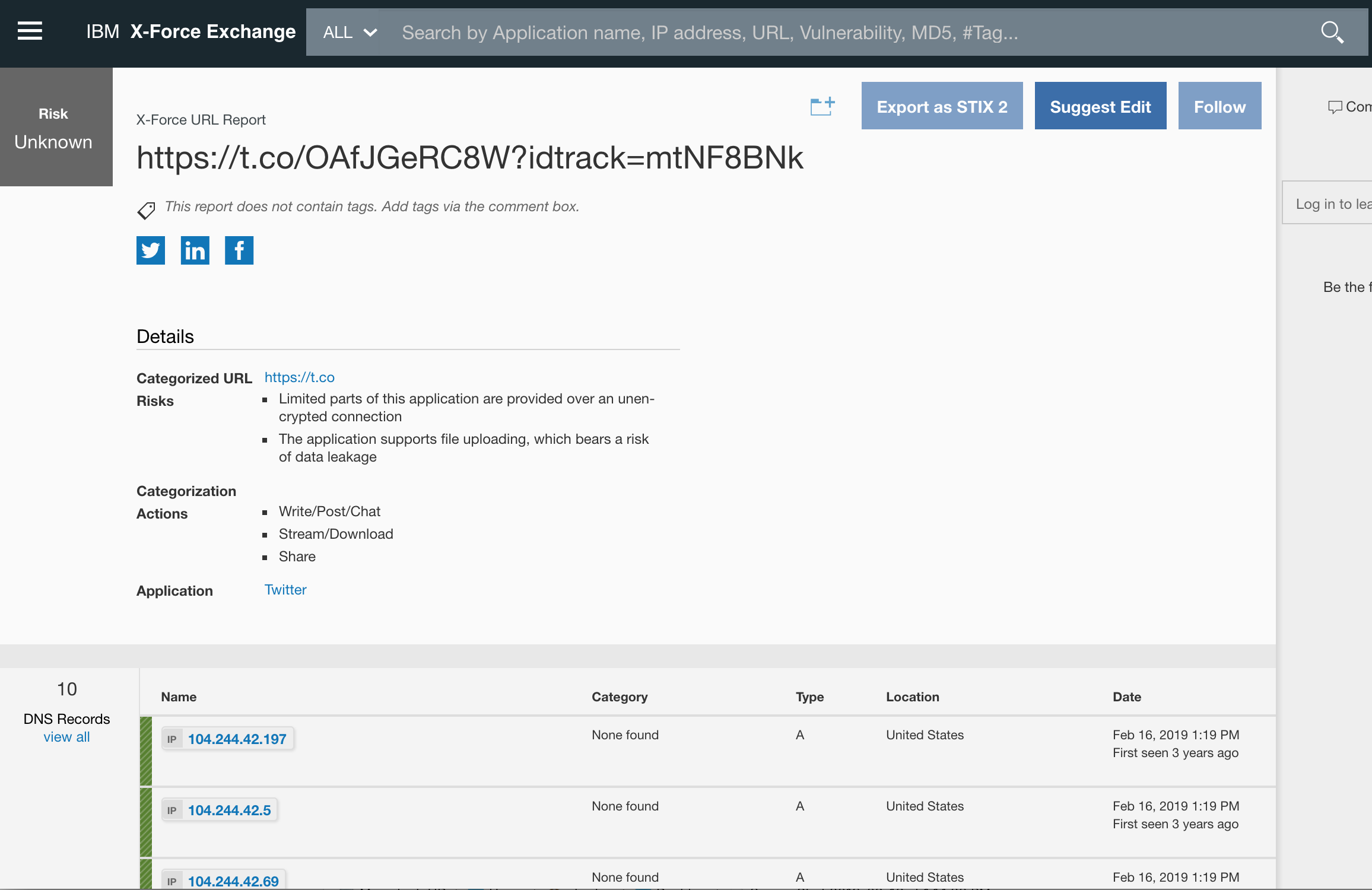
IBM X-Force
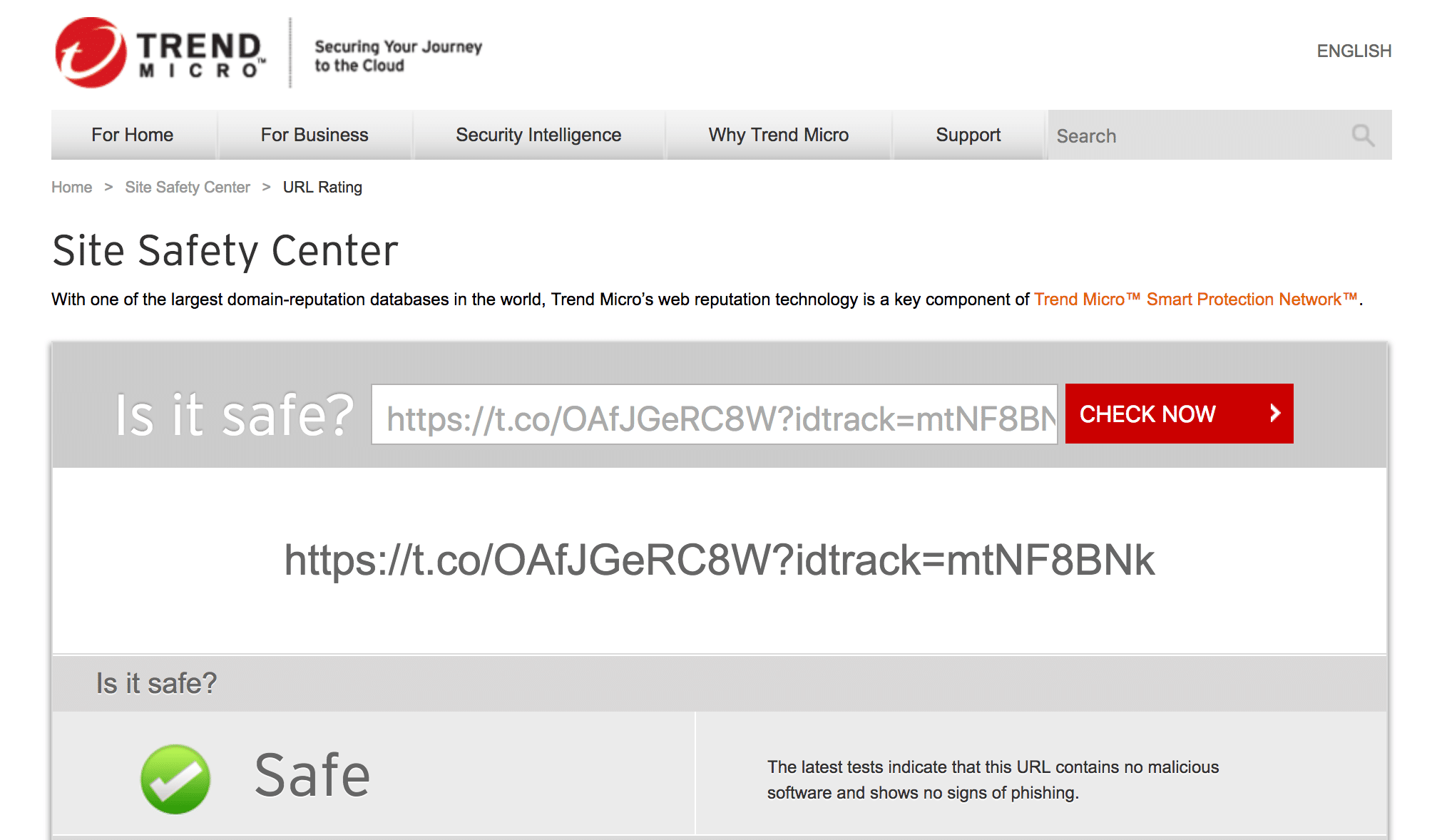
Trend Micro Site Safety
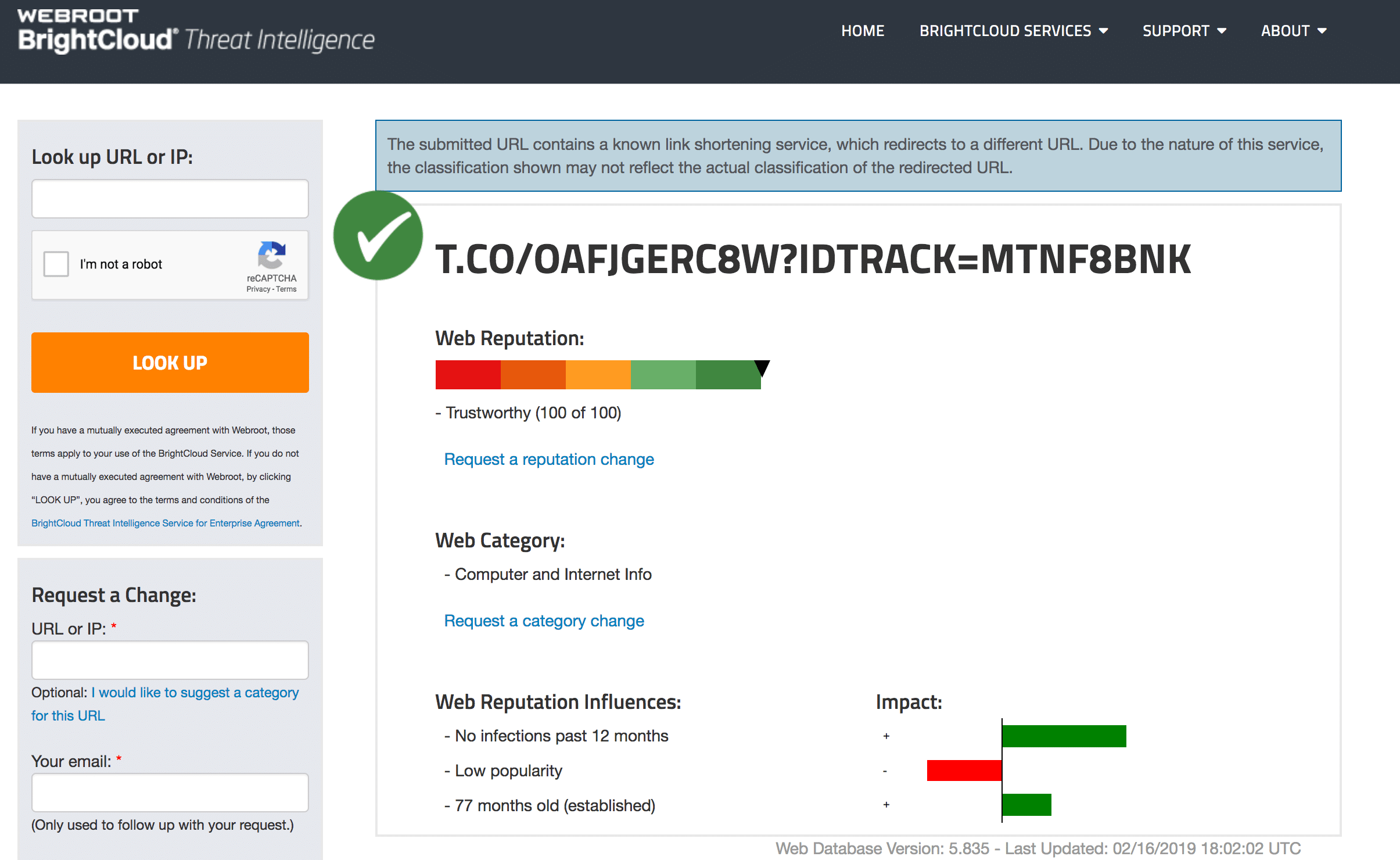
WebRoot BrightCloud Threat Intelligence
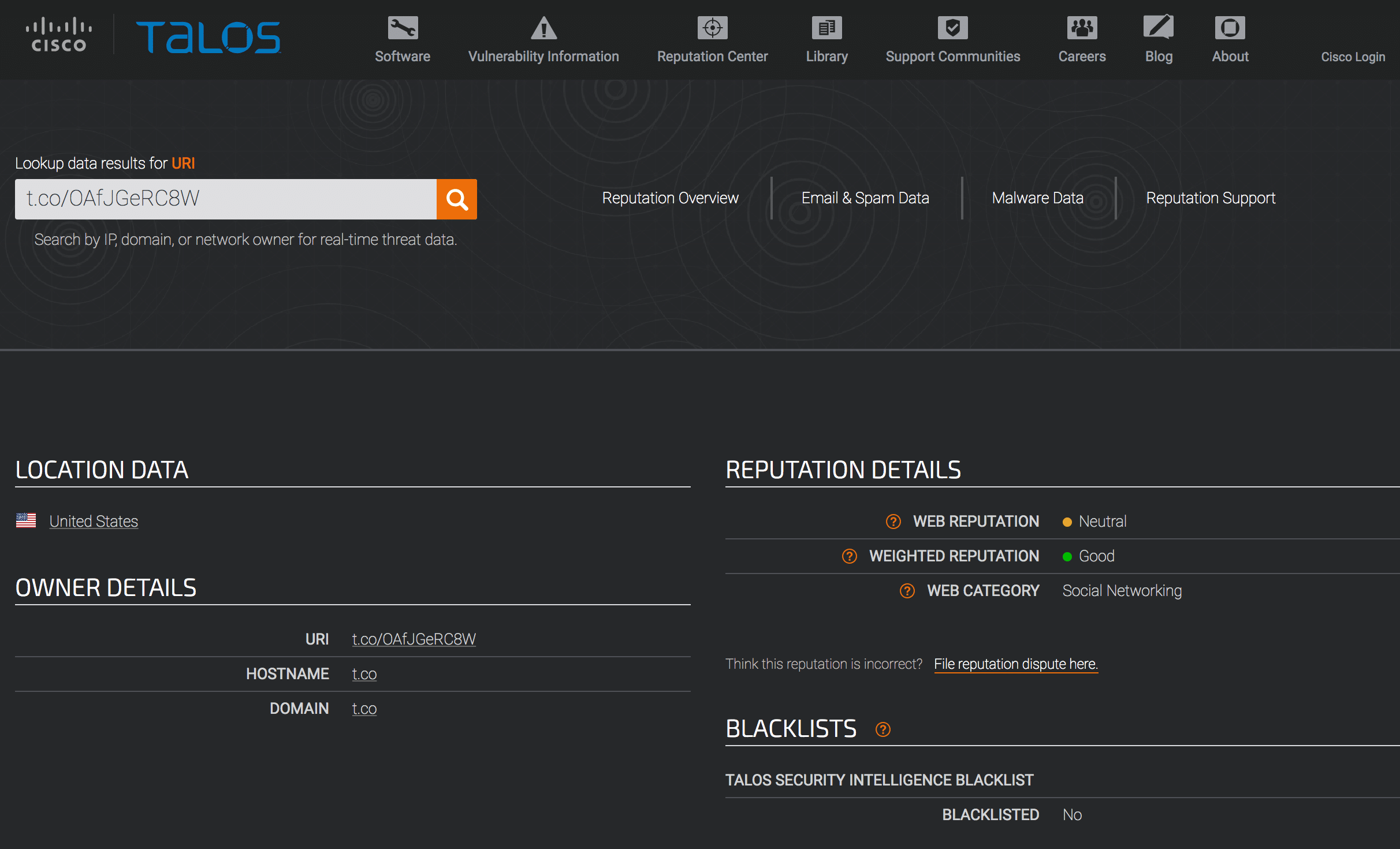
Cisco TALOS Intelligence
ZScaler URL Risk Analyzer
COMODO Web Inspector
Fortinet FortiGuard
Vade Secure IsItPhishing.Org
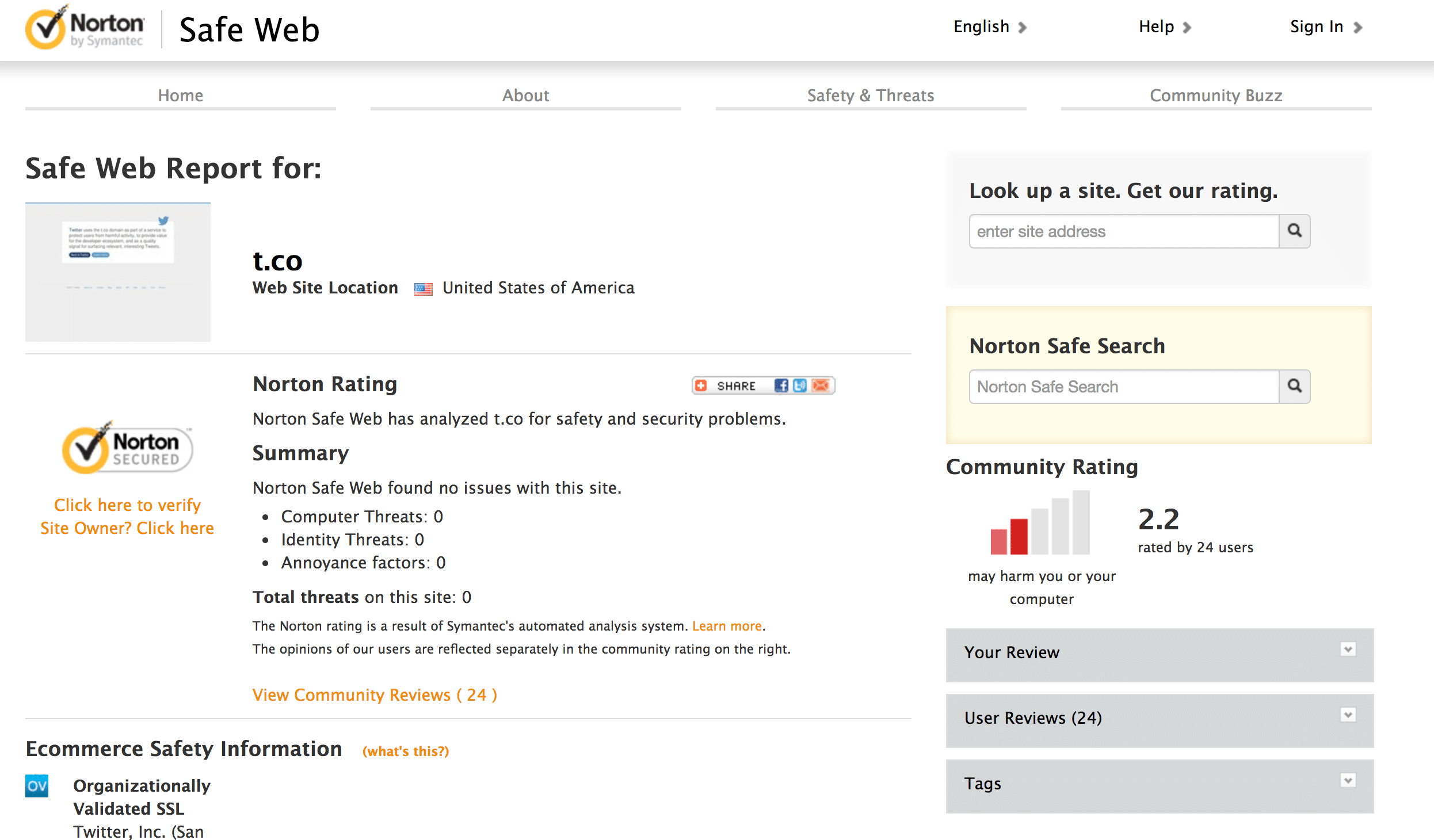
NORTON Safe Web
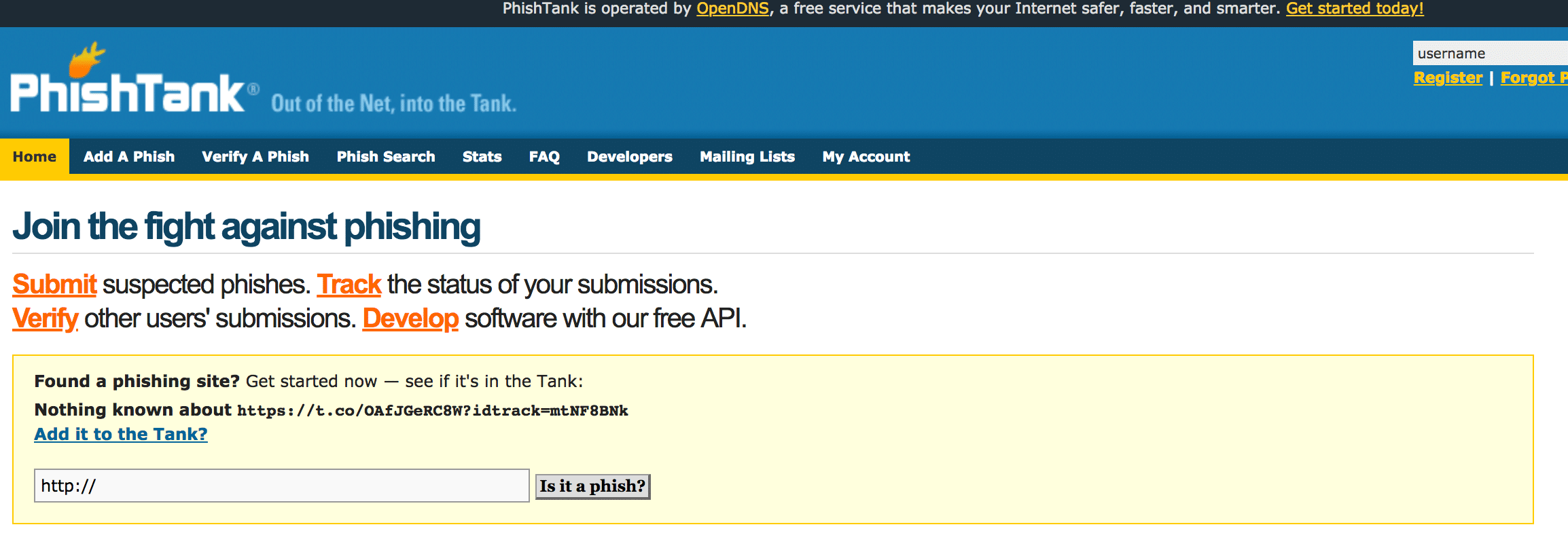
PhishTank


Recent Comments